
Related Items:
WSS Getting Started User Guide
Webroot DWP Configuration Guide
Guide Sections:
Using LDAP Settings to Add Users to Groups
This topic applies to user-based groups and describes how to add users to the group using LDAP synchronization. If you use Lightweight Directory Access Protocol (LDAP), you can use LDAP directory information to create users and update user information in the Web Security Service.
Secure LDAP servers
The Web Security Service works with secure LDAP servers if those servers have a certificate that is signed by a trusted source (not self-signed). If you are entering the connection information to the LDAP server in this situation, use ldaps://FQDN, where FQDN is the fully qualified domain name of the server that exactly matches your certificate.
Users added from LDAP
After you complete the LDAP setup in the Management Portal, the query on the LDAP directory is initiated in the next two-hour cycle, or if you click the Import Now button. Synchronizing with the LDAP directory imports user names and email addresses, and the users are added to the Users tab's list. The Web Security Service also generates a password for these users.
You might not see the updates to the Users tab until after the first minute of the next two-hour cycle. On the Users tab, the status of added users is Pending Activation until they subscribe to the service. Ensure that the group is set to receive email invitations, or that the page is enabled for the account, so that new users are notified and can register and change the system-generated passwords. You can click the Activate link on the Users tab, but users are not notified of the activation if you activate them in this way.
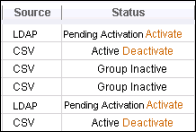
To complete the LDAP users' activation in the service, use one of these methods:
Select Automatically Send Email Invitation on the group's General Information subtab so that new users added from LDAP receive the invitation email containing the link for resetting passwords and can be subscribed to the Web Security Service. If authentication is required, these users enter their login name (the email address) and password.
Some accounts that use LDAP to add users might not supply email addresses for business reasons. Because email addresses are required, the Web Security Service creates the email addresses based on the LDAP user names and the Company Email Domain entry on the Accounts tab.
Use the Desktop Web Proxy (DWP) to create passwords automatically and activate these users. The DWP authenticates the users to the Web Security Service, if authentication is required. The DWP creates users and adds them to a default group, but does not change group assignments for LDAP users who have already been designated a group.
For more information about DWP, see the Desktop Web Proxy Configuration Guide.
Users deleted from the LDAP directory
If users are removed from the LDAP directory, the Web Security Service de-activates these users after time has elapsed. The elapsed time is based on the number of stale days (minimum is one stale day) you specify on the LDAP subtab. Using stale days requires enabling AutoReSync. After the stale days have passed, the users are automatically deleted from the service.
Email address changes
Email addresses in the Web Security Service are associated with the company's email domain and should be unique for each user. There are cases where an account acquires or merges with another company, and all users are moved to one email domain.
You might have two sets of users with different email addresses within one account. These are stored in the LDAP directory and created in the Web Security Service during synchronization. After the account has standardized all addresses and updated the LDAP directory, changes in LDAP also update the Web Security Service, as long as the email addresses are unique. If an affected user is browsing when the Web Security Service is updated by the synchronization, that user is prompted to log in again.
Group membership changes
If users are moved to different groups in the LDAP directory, they are also moved during LDAP synchronization. The move affects all users regardless of how they were entered into the Web Security Service. The group administrators are notified of the move.
Entering LDAP settings
The settings described here refer to attribute names that are standard LDAP terminology. Your LDAP administrator might have changed attribute names, however, so it's a good idea to verify the information before entering your LDAP settings.
Note: After you enter LDAP settings for one group, do not enter the same settings for another group. If you do, the first group is updated successfully, but importing into the second group using the same LDAP base DN fails and you'll receive an email notification of the failure.
To enter settings, you must have the permissions LDAP Settings for Manage Group, and Add for Manage User.
Note: Please ensure you have ports 389 (LDAP) or 636 (LDAPS) open to 66.35.53.175 (weblogin.webroot.com) to import and manage users via LDAP/LDAPS.
To enter LDAP settings:
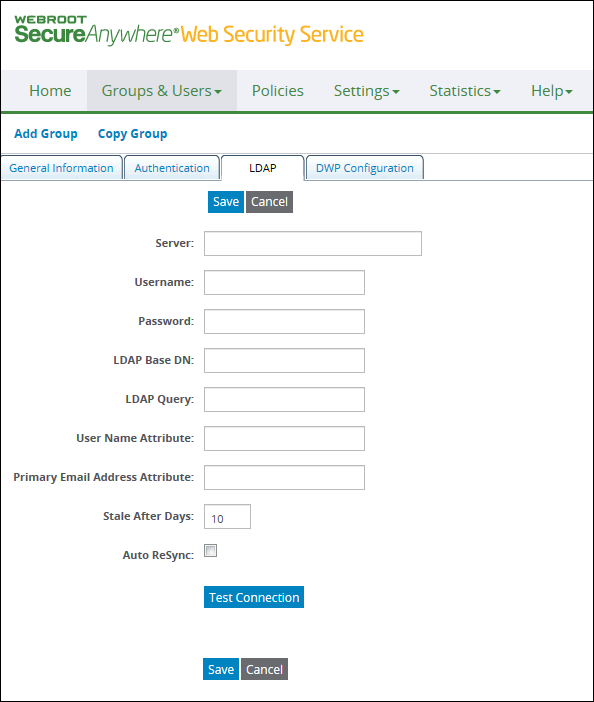
The subtab for Add Group includes the Import Now option; Edit Group does not.
Enter LDAP settings.
| LDAP Settings | Description |
| Server |
The IP address of the LDAP server in this format: ldap:// or if you have a secure LDAP server: ldaps:// The secure server must have a certificate from a trusted source, and the fully qualified domain name on the certificate must match your entry here. Self-signed certificates are not supported. |
| Username |
The username of the LDAP administrator. Allowed username formats include:
|
| Password | The password of the LDAP administrator. |
| LDAP Base DN | The LDAP base distinguished name (DN) that corresponds to this group. The query that searches the LDAP directory for user values starts from this base DN and continues downward. This value must be unique for each group that you populate using LDAP. |
| LDAP Query |
The LDAP query to get user names and email addresses from the LDAP directory to be added to the group. For example: (&(sAMAccountName=*)(mail=*)) |
| User Name Attributes |
The user name attribute in the LDAP directory. For example: sAMAccountName The service gets user name information from this attribute. |
| Primary Email Address Attribute |
The email address attribute name in the LDAP directory. For example: The service gets email address information from this attribute. |
| Stale After Days |
A number from 1 to 90. Defines the number of days to leave a user in the Web Security Service after the user is removed from the LDAP directory. The user is deleted from the Web Security Service after this number of days. The default is 10 days. A user that is removed from the LDAP directory is said to become 'stale' in the Web Security Service after a period of time. |
| Auto ReSync | Queries the LDAP server automatically and imports updates every two hours. Required if you specify Stale After Days. You receive email notification of the results. |
You cannot perform any actions on the portal, and other administrators cannot initiate another LDAP import, until the test has completed.
If the connection with the LDAP directory succeeds, the Management Portal displays the number of updates to be imported at the next synchronization.
If you are in Edit mode and you want to get updates from LDAP before the next synchronization, click Import Now. You must wait until the synchronization completes before you can do other tasks on the Management Portal.
Click Save.
The query is triggered at the first minute of every two hours starting at 12:01 a.m. The import updates the Users tab and populates the group's users list. You are notified of the success or failure of the import. An example of an error is that the LDAP update is trying to add an email address but the address is already used by another user, or the import is trying to add users that exist in the service.
On the Users tab, the Source column shows that this group of users was added using LDAP; their status is Pending Activation. Confirm that the Automatically Send Email Invitations option on the group's General Information tab is enabled, so that users are notified that they must subscribe to the system and enter their passwords. You can also use the Desktop Web Proxy (DWP) to automate user activation.
| Hosting Services | Customer Support | Additional Resources |
|
© 2017 Windstream Communications. All Rights Reserved. Privacy | Terms of Use | Hosting Policy | Legal Notices | Acceptable Use Policy | Digital Content License Agreement |

