Creating GPO to Deploy Webroot SSL Certificates for Firefox
This topic details the general steps, in order of execution, to install Webroot SSL Certificates for Mozilla Firefox specifically using Group Policy Management. The deployment steps described in this topic are:
- Create GPO to Deploy Webroot SSL Firefox Certificates
- Download Necessary Files
- Edit GPO
Important Information
- This topic only installs the Webroot SSL Certificates into all Mozilla Firefox profiles detected on a system. This topic does not cover certificate deployment for Internet Explorer or Chrome. For information on certificate deployment for IE and Chrome, see Creating GPO to Deploy Webroot SSL Certificates for IE and Chrome.
- If a user's Firefox profile contains other certificates besides the default ones, implementing this GPO will overwrite those leaving only the default and Webroot certificates.
- Enterprise Admin, Domain Admin, or equivalent rights are needed to complete this process. The DWP software only runs on the Windows Operating System.
- Customers are solely responsible for configuring their systems and networks in accordance with industry best practices.
To create GPO to deploy Webroot SSL certificates:
- Log onto your Windows Domain Controller with Domain Admin, Enterprise Admin, or equivalent.
- Start the Group Policy Management snap-in.
- Right-click the Domain or Organizational Unit where you want the Group Policy Object created and select Create a GPO in this domain, and Link it here.
The New GPO window displays.
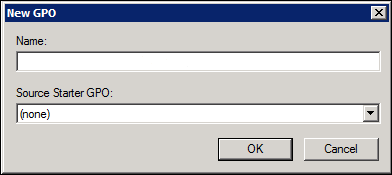
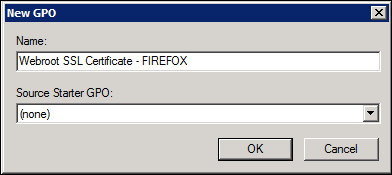
- In the Name field, enter a name for the GPO that identifies that this is for Webroot SSL Firefox management. For example, name it Webroot SSL Certificate - Firefox.
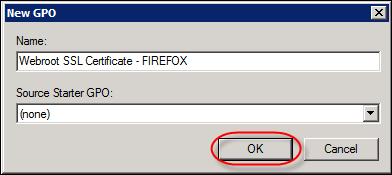
- Click the OK button.
- In a web browser, enter the following URL:
https://download.webroot.com/WSS/FirefoxGPO.zip
- Download and save the following four files to a network share to be used and accessed by the GPO.
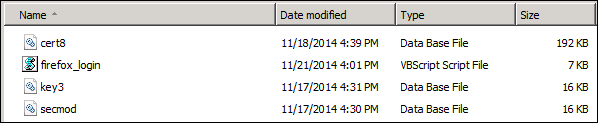
Note: This network share must have Server Operations permissions to properly function and be accessible by the Organizational Unit this GPO is assigned to.
- Save the fifth WR_FFcerts.adm file to your domain controller as this is the template to be imported in a later step.
- Navigate to User Configuration > Policies > Windows Settings > Scripts (Logon/Logoff).
- In the right pane, double-click Logon.
The Logon Properties window displays.
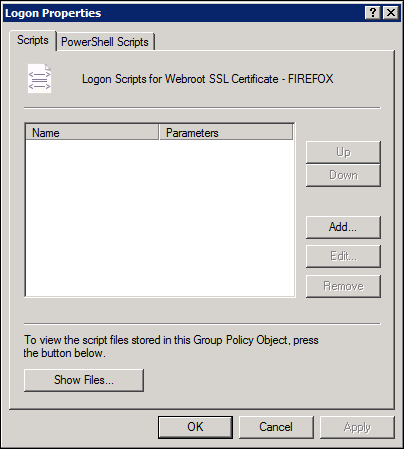
- Click the Add button.
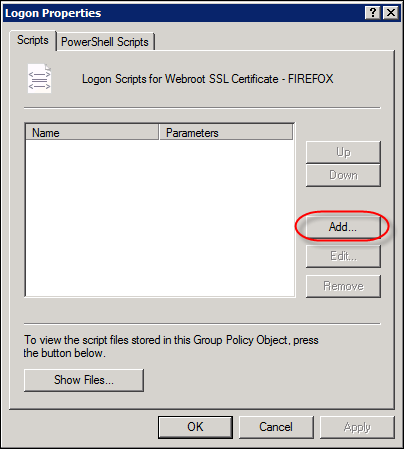
- Browse to the network share you previously stored the four files on and select firefox_login.vbs.
firefox_login.vbs is a script that runs at the time of logon, searches for all Firefox profiles on the system, and replaces the three .db (database) files used for certificate configuration.
- Import the ADM template into the newly created GPO by navigating to User Configuration > Policies > Administrative Templates.
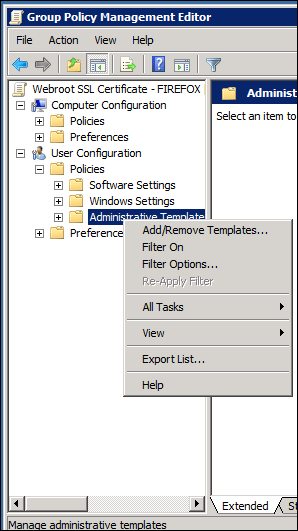
- Right-click and select Add/Remove Templates.
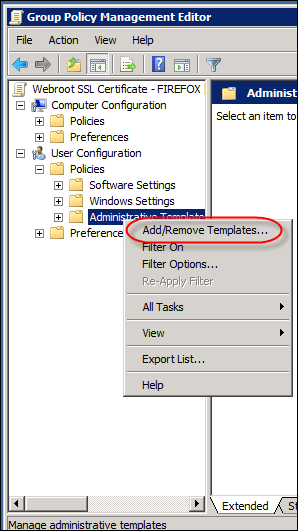
- Click the Add button and browse to the WR_FFcerts.adm file you downloaded earlier.
WR_FFcerts.adm is a custom template built by Webroot for managing SSL certs for Firefox users in a corporate environment.
- Open and configure this template by navigating to User Configuration > Policies > Administrative Templates > Classic Administrative Templates (ADM).
The Group Policy Management Editor window displays.
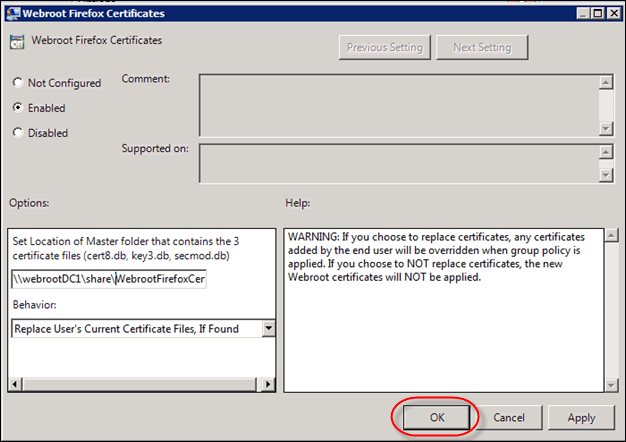
- In the right pane, double-click Webroot Firefox Certificates.
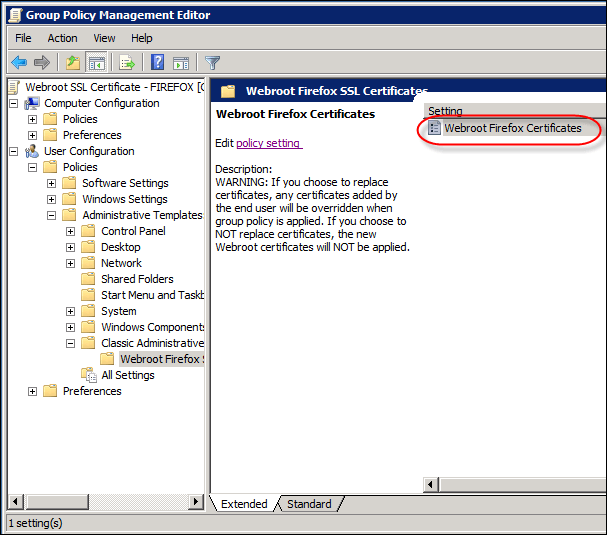
The Webroot Firefox Certificates window displays.
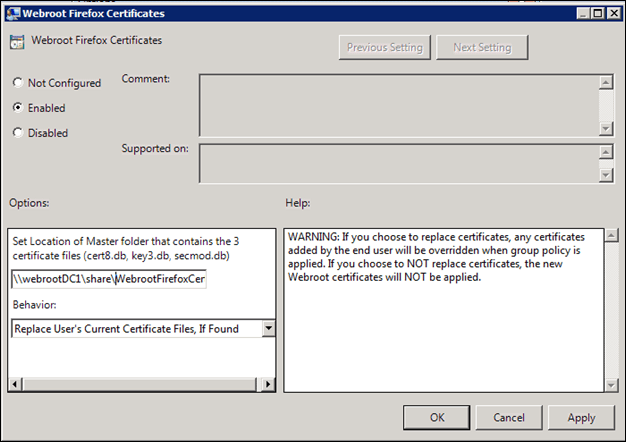
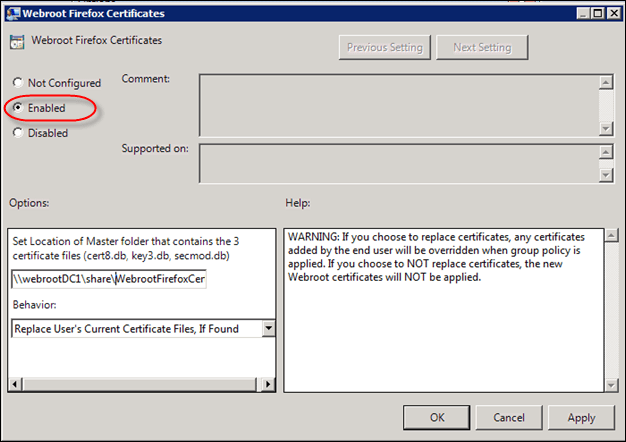
- Select the Enabled radio button.
- Set the UNC path of the network share you stored the three .db files in.
- To replace certificates, change the Behavior field to Replace User's Current Certificate Files, If Found.
- If you select this option, any certificates previously added by the end user will be overridden when group policy is applied.
- If you do not select this option, the new Webroot certificates will not be applied.
- Click the OK button.
- Once you complete the above steps, SSL Traffic Inspection will have to be enabled via policy in the Webroot Web Security Administrator Console.
For additional instructions, see Enabling SSL Traffic Inspection.















