
Related Items:
WSS Getting Started User Guide
Webroot DWP Configuration Guide
Guide Sections:
Adding User-Based Groups
You enter users in the Web Security Service by their valid email addresses. At group creation, authentication by user name is the default, as indicated by the Identify By setting.
Key features of user-based groups
A user-based group supports the following:
Authentication code
The Web Security Service generates a unique, read-only authentication code after you save a new group. The authentication code works with the Allow Mobile User Access setting to support mobile users who have the Desktop Web Proxy (DWP) installed. This code creates a user entry for mobile users in the group with the matching code.
Note: When installing DWP, you can use a command-line flag for the DWP installer where the beginning value of the Group Authentication Code (GAC) is set as if from the DWP user interface.
For example: msiexec -i dwpsetup.msi /q AUTHCODE=XXXXXXX
This addition allows customers to easily separate their users into groups at install time. Each group has a unique authentication code that can be used to configure DWP users to automatically be assigned to it.
The first time that mobile users access the Web Security Service from outside the corporate network, they are added to the group that uses the authentication code. Give mobile users the authentication code, so they can enter it into their DWP Credentials dialog.
Note: If mobile users don't enter this code in the Credentials dialog, DWP uses the group's Windows Domain as the basis for adding users to the group.
Methods for populating groups with users
You populate a group with users by a combination of the following methods:
To add a user group:
The Add page displays the General Information subtab.
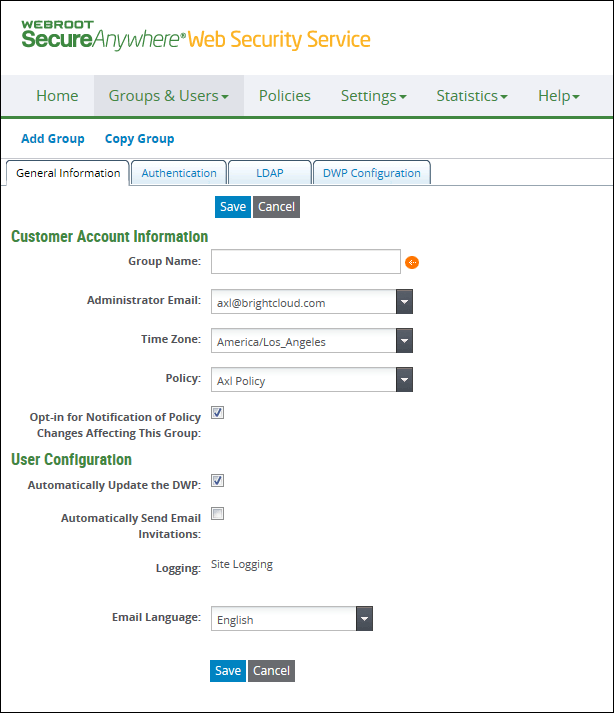
A new group inherits some default values from the Account subtab.
| Customer Account Information | Description |
| Group Name | Required. Enter a name of up to 30 characters. Valid characters are any combination from A to Z, a to z, 0 to 9; and the following special characters: ` ~ ! @ # $ % ^ & * ( ) _ + - = [ ] \ { } | ; ' : , . / < > ? Spaces are allowed. |
| Administrator Email | Identified by email address and defaults to the account's primary administrator. Select the administrator who is responsible for this group. |
| Time Zone | Defaults to the account's time zone. Select a time zone according to the group's geographical location, which may not necessarily be the same as the account's or administrator's time zone. This information is displayed on the grid. |
| Policy |
Required. Select a policy from the drop-down list. If no custom policy is defined, one of the out-of-the-box policies is applied, and you can change this later. This information is displayed on the grid. The policy might include quota definitions. Quotas are associated with time windows. If you later change the group's policy assignment with quotas using a different time window, the new time window takes effect. |
| Opt-in for Notification of Policy Changes Affecting this Group | Recommended. Keep this checkbox selected so that the administrator receives an email whenever a policy change affects this group. By keeping this option selected, the administrator will always know if another administrator made a change that affects their group definitions. |
| User Configuration | Description |
| Automatically Update the DWP | Ignored for IP groups. Used with Desktop Web Proxy. If disabled at the account, this option can still be enabled at the Group level. If selected, the end-user's system automatically receives DWP updates. Later, if the account is edited to disable this setting, the checkbox for the Group is cleared and disabled, to prevent entry |
| Automatically Send Email Invitations |
Ignored for IP groups. This setting is not required if you are using DWP. Select this checkbox to send the registration invitation to new users of this group. The default message provides the link to the Web Security Service and the temporary password to use. The text of the invitation is configurable in the Accounts tab's Emails subtab. If new users receive the invitation, they click the link within the email message and register in the service with a new password. Note: Select this setting if you are adding users through the LDAP directory, to enable those users to subscribe and enter their passwords. Otherwise, users remain pending and cannot authenticate themselves when prompted by the service. |
| Logging |
If the service provider enabled your account for full logging, you can modify this option:
|
| Email Language | Choose a language from the drop-down list. This language displays for emails received by all users in the group. |
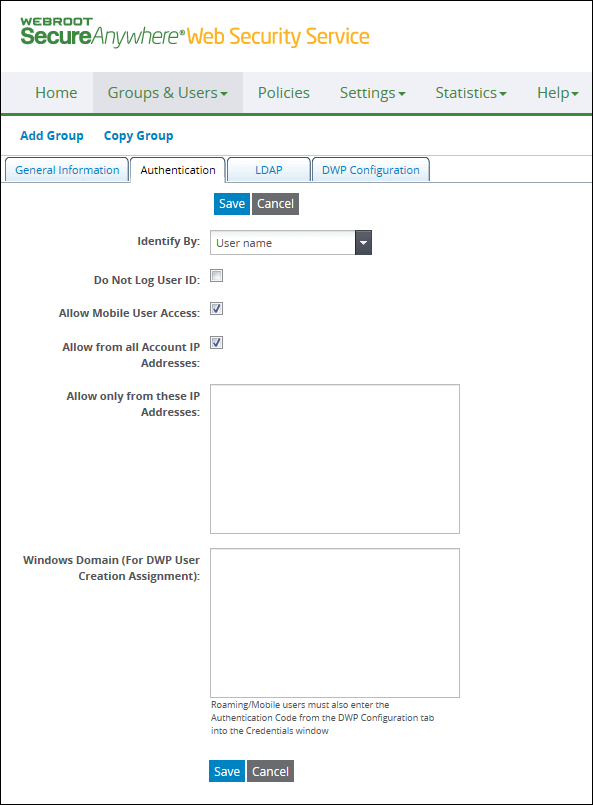
| Authentication by User Name | Description |
| Identify By | Keep User name. |
| Do No Log User ID | Select to prevent user-specific information from being logged for any members of this group. Select to protect an individual's privacy or to comply with legal requirements. |
| Allow Mobile User Access | Selected by default to support mobile users in this group. This option allows users in the group to connect to the Web Security Service while they are outside the corporate network, that is, from an unknown IP address. Users authenticate through a login prompt or through the Desktop Web Proxy. |
| Allow from all Account IP Addresses | Selected by default. |
| Allow only from these IP Addresses | Optional. Separate multiple domains with a comma. |
| Windows Domain (For DWP User Creation Assignment) |
Optional. Used with the Desktop Web Proxy (DWP). If a user does not yet exist in the service, DWP enables the automatic creation of that user in the group. Enter the Windows domains in the format abc.com. Separate multiple domains with a comma. This should match the domain name displayed for the user on MyComputer's System Properties dialog. The process of determining group assignment for DWP users follows this sequence:
Note: After you save a group, the Web Security Service generates a unique Authentication code for the group. This code is used for DWP users. |
| Hosting Services | Customer Support | Additional Resources |
|
© 2017 Windstream Communications. All Rights Reserved. Privacy | Terms of Use | Hosting Policy | Legal Notices | Acceptable Use Policy | Digital Content License Agreement |

