
Related Items:
WSS Getting Started User Guide
Webroot DWP Configuration Guide
Guide Sections:
About Logs
The Management Portal provides logs that show up-to-date data about traffic flowing to and from an account through the Web Security Service. For a given date, the logs reflect data up to the current time, with a latency of approximately 15 minutes (depending on the service load).
Note: To use the Logs tab, you must have the View permission for Manage Log.
These log categories are available:
From the Logs tab, you can configure logs to display data at a granular level, such as individual groups, exact dates and times, specific URLs, and so on.
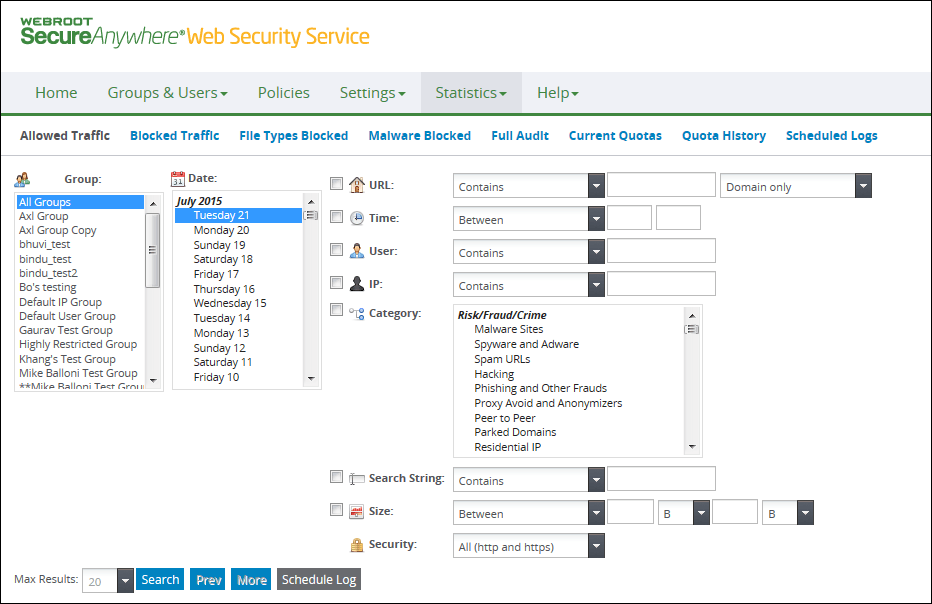
By default, ten records are shown. Logs are based on all groups for the current day with no filters defined. You can view additional log records by changing the Max Results value and then clicking Search. The search filters on the upper right of the page provide options to narrow the search. After selecting a filter, enter the required value or text, then start your search.
Full versus Site logging
The way your account is set up for logging determines the level of detail that is displayed in Full Audit.
| Data in the Logs | Description |
| Date | The date when the Full Audit log was generated, based on the administrator's time zone. You can access logs from as far back as 90 days before the current date. |
| Time | The time when the log was generated, based on the administrator's time zone. |
| Group Name | The group to which the user belongs. |
| User Name | The user's login name (email address). |
| Category | The accessed site's category. |
| URL | 'Full' logs URLs typed on the address box plus all URLs required to render a page, such as links, images, and others. 'Site' logs only the URL typed on the browser's address box. |
| Search Engine String | The text typed in the search engine for web searches. |
| File Type | The file type found in the Policies' File Types subtab. |
| Content Type | 'Full' logs all MIME types. 'Site' logs text and SSL types only. |
| Size | The downloaded file size in bytes. A size of 0 indicates that the file was blocked. |
| Malware Name | The name of the detected malware, for example, storm.gen. If blank, no malware was detected. |
| Malware Type | The detected malware category. For example, a malware called storm.gen would have the category Trojan Horse. If blank, no malware was detected. |
| Malware Direction | Displays inbound if the malware was downloaded, or outbound if the malware was uploaded. If blank, no malware was detected. |
Text searches
See the following table for how to use text searches in logs.
| Text Searches | Description |
| If your URL text string contains special characters |
If you search on URL text strings that contain special characters, insert the backslash character (\) before the special character so that the search works correctly. These special characters require the backslash (\): & ? ^ . ( ) [ ] + | For example, if the search is for records with URLs that contain the literal string &coke, enter a backslash before it: \&coke. |
| Using the Equals criteria |
If you use the Equals criteria, consider the following:
|
| URL Searches | When searching for domains and domain paths, the ? (question mark) character serves as the separator between the URL path and parameters; therefore, anything after the ? is ignored. For example (partial URL shown): http://streamerapi.finance.yahoo.com/streamer/1.0?s=^DJI, USD=X&o=^DJI Even if you enter the above in the search field and insert the backslashes accordingly, the search ignores this part of the search string because it occurs after the ? character. |
Group data
The logs display data for current groups, and for groups that were deleted within 30 days. Deleted groups are prefixed by two asterisks and suffixed by the date they were deleted. If the group is deleted and re-created several times on the same day, the same-date suffix is used. In this case, you see multiple instances of the deleted and re-created group in the list. The selection list sorts the groups alphabetically by group name. The prefix ** is not considered part of the group name.
Log retention time
The Web Security Service keeps your data for 12 months, including data on deleted groups. For each search, the result set can include data from a maximum of 90 days. Your search doesn't have to specify contiguous 90-day dates. You can specify non-contiguous dates as long as the total number of days doesn't exceed 90. The Web Security Service totals the number of days specified on your search. If the total days exceed 90, a message directs you to run your queries on 90 days or fewer.
| Hosting Services | Customer Support | Additional Resources |
|
© 2017 Windstream Communications. All Rights Reserved. Privacy | Terms of Use | Hosting Policy | Legal Notices | Acceptable Use Policy | Digital Content License Agreement |

