
Windstream offers Unified Email Management (UEM) through it's partnership with Mimecast. Unified Email Management service offers everything an enterprise needs to better manage their Microsoft Exchange Email infrastructure in a ready-to-use online Software as-a-Service (SaaS) solution, removing the growing risks and complexities of business email management with a single platform.
How the Cloud Has Changed Email Archiving Forever
Resetting Your Email Security Strategy
 Targeted Threat Protection - URL Protect Best Practice
Targeted Threat Protection - URL Protect Best Practice
 Creating / Changing a URL Protection Definition
Creating / Changing a URL Protection Definition
 Creating / Changing a URL Protection Policy
Creating / Changing a URL Protection Policy
 Creating / Changing a URL Protection Bypass Policy
Creating / Changing a URL Protection Bypass Policy
 Displaying Targeted Threat Protection - URL Protect Logs
Displaying Targeted Threat Protection - URL Protect Logs
 The Targeted Threat Protection - URL Protect Dashboard
The Targeted Threat Protection - URL Protect Dashboard
 Targeted Threat Protection - Attachment Protect Best Practice
Targeted Threat Protection - Attachment Protect Best Practice
 Targeted Threat Protection - Attachment Protect Dashboard
Targeted Threat Protection - Attachment Protect Dashboard
 Creating / Changing a Attachment Protection Definition
Creating / Changing a Attachment Protection Definition
 Creating / Changing an Attachment Protection Policy
Creating / Changing an Attachment Protection Policy
 Creating / Changing a Attachment Protection Bypass Policy
Creating / Changing a Attachment Protection Bypass Policy
 Targeted Threat Protection - Impersonation Protect Best Practice
Targeted Threat Protection - Impersonation Protect Best Practice
 Creating / Changing an Impersonation Protection Definition
Creating / Changing an Impersonation Protection Definition
 Creating / Changing an Impersonation Protection Policy
Creating / Changing an Impersonation Protection Policy
 Creating / Changing an Impersonation Protection Bypass Policy
Creating / Changing an Impersonation Protection Bypass Policy
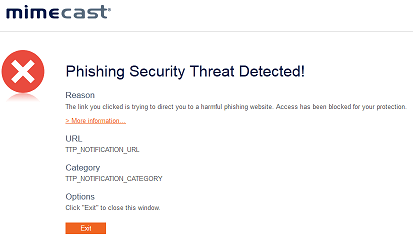
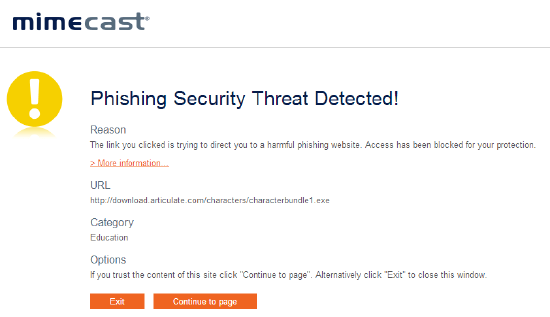
The Targeted Threat Protection - URL Protect feature re-writes all URLs embedded in an email, including those in .TXT and .HTML attachments, and performs a layered security check on the destination site when a user clicks on the link.
Depending on your configuration, the following behavior is expected:
The upsurge in 'whaling' attacks, usually targeting an organization's upper management, means additional protection is required for threats that do not contain attachments or URLs. Traditional spam filtering systems are unable to detect these as suspicious due to the minimal content in most of these attacks. Targeted Threat Protection - Impersonation Protect solves this by looking for combinations of key identifiers commonly found in these attacks.
Additionally, you can help users identify all emails as coming from an external source regardless of any identifiers triggering. This will be a banner added to the top of each inbound email.
Details on how to set up Targeted Threat Protection - Impersonation Protect can be found under  definition and
definition and  policy.
policy.
As Targeted Threat Protection - Impersonation Protect forms part of Mimecast's Targeted Threat Protection suite, it provides security protection against malware, phishing, whaling, impersonation, and socially engineered phishing attacks. You must have another product from this suite (e.g. Targeted Threat Protection - Attachment Protect or Targeted Threat Protection - URL Protect) to use the Targeted Threat Protection - Impersonation Protect product.
Targeted Threat Protection - Attachment Protect provides advanced security protection for file attachments in email messages. It can be configured in the following ways, in line with the needs of your organization:
Files that are either unreadable, encrypted, or greater than 50 MB in size, can't be processed by the sandbox. Additionally, safe files created by Targeted Threat Protection - Attachment Protect can't be larger than five times their original size, and can never exceed 30 MB whichever comes first. The maximum size of a file that can be transcribed by Targeted Threat Protection - Attachment Protect is 15 MB.
We recommend you create attachment policies to handle these files. Failure to do so means these files are placed on Administrator Hold. See the Managing Attachments Overview page for further details.
Targeted Threat Protection - Attachment Protect requires the administrator to create definitions and policies for the different attachment scenarios. Administrators can configure any combination of the modes and apply to all users or selected users / groups.
Supported File Types
Targeted Threat Protection - Attachment Protect provides protection across the following file types:
This also include attachments in the following archives:
When an email containing an attachment that has been put on hold as a result of an Attachment Protection policy finding it unsafe, the recipient receives an email detailing what has happened. If they wish, the recipient can request the administrator to release the original attachment to the user.
What if the Original Attachment Contains Malicious Code?
If an email attachment is found to contain malicious code, it is blocked and not sent to the recipient. Instead the recipient receives an email from Mimecast informing them of the block, and displaying details of the email, its attachment, and the policy that blocked it. For example:
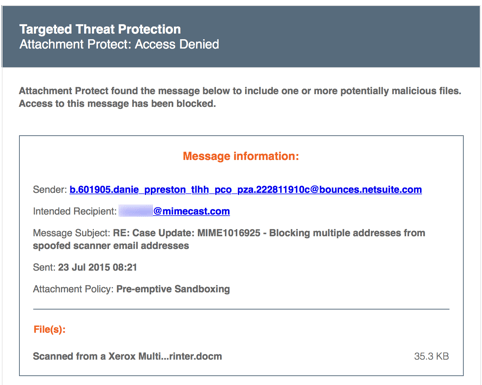
How Does Targeted Threat Protection - Attachment Protect Handle Messages Held as Spam?
When a message comes in with the attachment, it immediately goes into the Targeted Threat Protection - Attachment Protect sandbox for immediate scanning. If it's to be held, it is sent to the spam hold for release. Depending on your Attachment Protection definition, you'll have access to download the original file from the sandbox once the message has been released along with the attachment.
Safe or Unsafe Files
The Administrator has full control over what happens to blocked attachments. Whilst the recipient can request for an attachment to be released, it is the Administrator's ultimate responsibility to allow this. They can release the:
| Hosting Services | Customer Support | Additional Resources |
|
© 2017 Windstream Communications. All Rights Reserved. Privacy | Terms of Use | Hosting Policy | Legal Notices | Acceptable Use Policy | Digital Content License Agreement |

